
The One Percent
The cyber ecosystem is under relentless attack.
The cyber ecosystem is under relentless attack with increasing intensity, volume, severity and sophistication. Corporations have sophisticated firewalls and other countermeasures; individuals are largely helpless. Some think they have a plan against this threat, but the reality is that security is never 100 percent and attackers, the one percent, always have the advantage. But there is a path forward – by unifying security, political, social, and economic measures.
The One Percent

Cybersecurity provider NTT Security reports that five countries are the most common sources to 50 percent of global cyberattacks (Figure 1).
Akamai states that two-thirds of Distributed Denial of Service (DDoS) cyberattacks originate in ten countries. Symantec, another provider, adds 13 more countries for a total of 23 countries, which are homes to the worst cyber offenders and who are responsible for two-thirds of all malicious internet activity.
The FBI states the odds of a criminal getting caught in the United States are approximately 1 in 5. Applied to the 0.7 percent incarceration rate in the US, 693 per 100,000 people, the second highest global incarceration rate, the criminal population may be five times higher, up to 3.5 percent of the US population. Since FBI crime statistics are credible, represent crime in ethnically and racially diverse geographical areas, and every country has a criminal element (either incarcerated or inclined to commit crimes), it is not a stretch to say that up to 3.5 percent of the global population are either criminals or have criminal tendencies.
Since malicious/criminal behavior is no less prevalent online, up to 3.5 percent of internet users may be engaged in cyber-enabled crime such as malicious hacking, fraud, the purchasing of illegal drugs and child sexual exploitation. Britain’s National Crime Agency states that the average hacker age is now 17. This age falls in the 15-24 age group, which represents 26.5 percent of internet users. By extrapolation, malicious hackers may account up to 0.9 percent of internet users.
The Diagnostic and Statistical Manual of Mental Disorders (DSM-5), the definitive diagnostic reference for mental health practitioners, states that Antisocial Personality Disorder (ASPD) is:
“a pervasive pattern of disregard for and violation of the rights of others…as indicated by repeated lying, use of aliases, or conning others for personal profit or pleasure…lack of remorse, as indicated by being indifferent to or rationalizing having hurt, mistreated, or stolen from another.”
Malicious or criminal behavior fits the DSM-5 ASPD and may run as high as 5.8% in men and 1.9% in women. With men and women representing 53 percent and 47 percent respectively of global internet users, it is estimated that up to 4 percent of internet users have ASPD. Considering the average hacker age (15-24 age group), it is estimated that up to one percent of internet users may be malicious hackers, a finding which approximates the previous 0.9 percent. The DSM insight suggests that there are more male than female hackers, by a ratio of 3 to 1. Based on internet demographics, a global cybercriminal population of 46 million is not beyond the pale.
A Framework for Social Change
Criminal activity is typically a country problem. What sets cybercrime apart from usual criminal activity is that hacking knows no borders. Security measures alone will not work – this approach requires the willingness to apply extreme measures, a solution society would view repressive on a 17-year old hacker. A better approach and one grounded in history, aims to marginalize and ultimately co-opt hackers through unified security, political, social, and economic measures.
Legitimacy, the right and acceptance of authority and of exercising power, is critical to achieving change. Politicians and civil leadership must collectively reinforce that the judicial system and law enforcement actions against malicious hackers are appropriate uses of power vested by legally established governments. On a cautionary note, history has shown that excessive use of power can undermine legitimacy.
For this reason civil institutions must be part of the solution. For a model consider Sweden’s drug policy, which includes preventive measures involving schools, clubs and associations, social services, psychiatric services, etc. Measures are supplemented by targeted interventions aimed at individuals and groups in risk zones. Outreach and support programs under umbrella organization such as Health and Human Services can intervene; so can community anchors such as churches, synagogues and mosques. Surveillance raises privacy issues, but these are manageable by effective governance and compliance.
Capabilities Not Met
More than 1-in-5 businesses have no confidence in responding to a cyberattack. Lack of confidence points to shortcomings in people, process and technology to deal with cyber events. Budgets for cybersecurity vary, but large organizations should target 0.4 percent of revenue. Some spend more. Microsoft is estimated to spend twice that. With global GDP at US$ 86 trillion, this would suggest global cybersecurity spending should be US$ 344 billion. Businesses spend a third of this amount – research firm Gartner estimates 2019 cybersecurity spending amounted to US$124 billion. With cyberattacks costing US$1 trillion annually, cybersecurity spending should increase.
Insurers have a role to play in protecting client businesses from risks. Cyber policy coverage provides services against attacks and immediate access to legal and technical resources, often coaching businesses through an attack. Insurers can assess the insured to a cybersecurity maturity framework. Assessments benefit multiple parties. The insurer benefits by setting rates based on risk. The insured can remediate identified cyber gaps, and once resolved, should qualify for a lower premium. Assessments are also important to governance and compliance, providing assurance to company stakeholders and shareholders.
Historical Context
Insurgents and malicious hackers share some characteristics – first mover advantage, often control of the narrative with news headlines, the weak against the strong, and control through subversion. Given the similarities, we may be able to draw on counterinsurgency lessons learned.
One counterinsurgent per 357 in a population in a peaceful situation and one per 40 in hostile environments is generally accepted as the minimum. The most recent US lesson in Iraq provides guidance, particularly what not to do. Despite quickly defeating Iraqi military forces, the US never adequately planned for the occupation of Iraq and its presence was never large enough to maintain civil order. Decisions to disband the Iraqi Army and the de-Baathification of the government were incredibly misguided and contributed to subsequent chaos. US forces never approached a 40 to 1 counterinsurgent to population ratio (Figure 2).
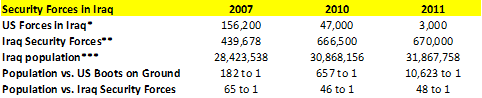
With loyalties divided along ethnic lines and despite sizeable numbers, Iraqi Security Forces were never a competent or cohesive force under the divisive leadership of Prime Minister Nouri al-Maliki (2006-2014). Since then, even under Adnan al-Zurfi, these issues, as well as lack of governance and nepotism, continue to negate the effectiveness of Iraqi Security Forces.
In direct contrast, Winston Churchill was quick to grasp the counterinsurgency challenges Britain faced during the Malayan Emergency (1948-1960). In one of his first actions as Prime Minister
(1951-1955, his second time), he appointed General Sir Gerald Templer with greatly expanded command and control authority to defeat the Chinese Communist guerrillas. Templer deployed “clear and hold” operations and population-centric (“winning the hearts and minds”) tactics, the basis which remains a successful counterinsurgency strategy. In contrast to the US involvement in Iraq, security forces were very visible during the Malayan
 Emergency amounting to one member for every 16 civilians (Figure 3). It also helped that Chinese guerrillas had limited support among the Malay population (55 percent Malay, 35 percent Chinese, 10 percent Indian in 1957) and Malays firmly supported the government including heavily enlisting in the security forces.
Emergency amounting to one member for every 16 civilians (Figure 3). It also helped that Chinese guerrillas had limited support among the Malay population (55 percent Malay, 35 percent Chinese, 10 percent Indian in 1957) and Malays firmly supported the government including heavily enlisting in the security forces.
Closing Thoughts
By any assessment, the fabric of society is under siege. Malicious hackers are threatening society by subverting a critical means of communication. While the role of government can be debated, unequivocal is its responsibility as a protector, to provide the safety of law and order, protecting citizens from each other and against foreign enemies. Its obligation extends to essential economic infrastructure including cyber space. The fight against hackers requires marshaling society’s resources into a coalition front. And for that we need, foremost, political leadership.
Jeffery Mayger is an information Security Consultant at Concord. His background includes Chief Information Security Officer (CISO) for global mining company Sibelco. In addition to his B.S in Mechanical Engineering, Mr. Mayger also holds a Master of Business Administration (MBA) from the University of Texas, is a Certified Information Security Professional (CISSP), Certified SCADA Security Architect (CSSA), and a designated Payment Card Industry Professional (PCIP). He can be contacted at jeffery.mayger@concordusa.com.
Published in Circuit Magazine Issue 53.