
Think Twice Before Clicking
Your mouse cursor moves erratically on the control console as you monitor the water treatment plant. You shrug it off, but it happens again, and this time the cursor moves systematically. Screens open and close; it appears the system is being searched. Then the control screen for the plant’s pH adjustment opens and the settings change. You realize that your utility is under attack, and you enact emergency procedures.
Real-World Consequences
Online attacks like this scenario aren’t hypothetical these days. For example, swift action by an operator at a water utility in 2021 prevented disastrous consequences as an unknown attacker tried to poison the water of a utility’s system by significantly increasing the concentration of sodium hydroxide used to treat acidity. Left unchecked, this attack on a utility’s customers could have led them to ingest high concentrations of a corrosive chemical that could have led to severe pain, vomiting, and internal hemorrhaging.
Community water systems in the United States provide service to more than 286 million people, and ensuring their water is safe, secure, and reliable is a constant challenge. Insufficient budgets, lack of dedicated information technology and cyber staff, limited cyber expertise, inadequate visibility, and ineffective defensive tools can all contribute to potentially catastrophic situations.
Attacks increasingly exploit ransomware, a type of malicious software designed to block access
to a computer system until a sum of money is paid. In the summer of 2021, ransomware criminals hacked a major US water utility serving nearly two million people. Although the utility had backup processes and was able to restore operations, other utilities hit with ransomware may not be so prepared.
Critical infrastructure is a compelling target for attackers. One compromised password prompted the Colonial Pipeline, a US oil pipeline system that originates in Houston, to shut down in the spring of 2021. The pipeline supplies 2.5 million barrels of fuel per day to the eastern United States, and the shutdown resulted in a spike in fuel prices and long lines at service stations. Internationally linked criminals used ransomware to extract 100 gigabytes of data and threatened to leak the data if the ransom wasn’t paid. Colonial paid $4.4 million in return for a decryption tool to unlock its computer systems.
Common Concerns
Attackers have several ways to deliver ransomware, but phishing email campaigns are most often used because it is generally easy to deceive people. Despite significant awareness efforts to curb phishing, it only takes one person to click on the wrong link to bring a utility down. But why?
Phishing is a form of social engineering, a broad term used to describe a range of techniques to trick people into giving criminals what they want. According to Verizon’s 2021 Data Breach Investigations Report, 92% of breaches are caused by social engineering. Infamous ex-hacker turned cybersecurity consultant Kevin Mitnick attributes successful social engineering attacks to five traits: greed, curiosity, urgency, helpfulness, and fear.
Cyber criminals exploit human weaknesses, and they know what works. Mental health practitioners also understand what drives human behavior, and among these is the pursuit of wealth. Hackers are keenly aware of this, and thus it’s a frequent theme in phishing attacks. According to phishing mitigation company KnowBe4, LinkedIn phishing messages have dominated the social media category for the past three years, with variations including “people are looking at your profile” or “add me”.
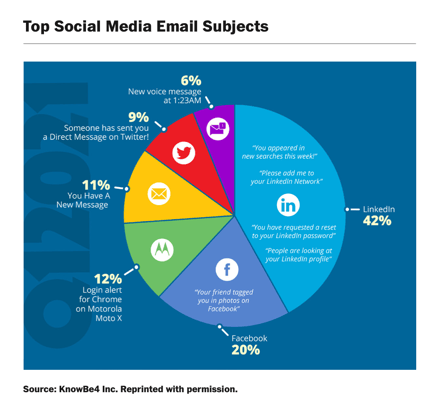
Furthermore, almost one-third (31%) of phishing emails are about password checks. According to a February 2021 article from Infosec, “11 Phishing Email Subject Lines Your Employees Need to Recognize,” the most-clicked general email subject lines include the following:
- Billing information is out of date
- Payroll has been delayed
- Updated vacation policy
- Office reopening schedule
- Confidential information about COVID-19
- Your meeting attendees are waiting!
- Employee raises
- Dropbox: Document shared with you
- Attention: Unusual account activity detected!
- Earn money working from home
Beware of Warning Signs
With breach costs often amounting to millions, there is real value in prevention, and user awareness training is a key component in preventing phishing from being successful. Be particularly cautious anytime you see the following indicators:
- Sensitive information requests via email. Signs of phishing include requests for passwords, credit card information, credit scores, or tax numbers, messages that direct you to a link from which you need to login.
- Email messages that don’t use your name. Generic salutations should give you immediate concern, such as “Dear Valued Member,” “Dear Account Holder,” or “Dear Customer."
- Suspicious email address. By hovering your mouse over the “from” address, beware of alterations such as additional numbers or letters (e.g., instead of john@ paypal.com, you see john@ paypal23.com or manager@ gmail123.com).
- Spelling mistakes. Legitimate emails are well written (well, mostly).
- Website redirects. Clicking anywhere in the email may open a fake webpage, so be careful.
- Unsolicited attachments. Any unsolicited email with attachments is a dead giveaway for hacking; legitimate companies will direct users to download files from their own websites.
- Links that don’t match legitimate URLs. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it.
Phishing is particularly dangerous, yet according to KnowBe4, about 31% of untrained end users fail a 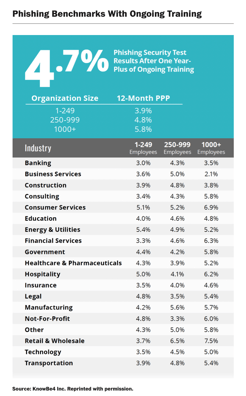 phishing test. Even with training programs in place, organizations still often struggle, and phishing click rates currently average 4.7%. Energy and utility organizations range above average, between 4.9% and 5.4%, and government organizations range between 4.2% and 5.8%.
phishing test. Even with training programs in place, organizations still often struggle, and phishing click rates currently average 4.7%. Energy and utility organizations range above average, between 4.9% and 5.4%, and government organizations range between 4.2% and 5.8%.
According to Avanan’s 2019 Global Phish Report, one in 99 emails involve phishing. Also, according to data in the aforementioned Verizon report, 36% of breaches start with phishing, and 10% of breaches involve ransomware.
With office workers receiving an estimated 120 emails daily, a small 80-employee organization receives just under 50,000 emails per work week. Even if employees are diligently trained on how to recognize phishing emails and achieve a 5% click rate, the organization may be hit with as many as eight breaches per week and three ransomware attacks per month. Getting attacked with ransomware is no longer academic; it may not happen today or tomorrow, but a cyberattack will happen sometime.
Cybersecurity Defense
A layered, in-depth cybersecurity defense is needed to counter attacks. It’s particularly important to have identification and response controls to notify a utility that an attack is occurring. Layered defenses and configured controls can lessen an attack’s severity; they may even determine whether a utility continues to operate. There are four vital controls:
- End-point detection and response
- Intrusion detection and prevention systems
- Security information event management for aggregating and analyzing network logs
- Trained personnel dedicated to monitoring the network environment
Given tight budgets, as well as the complexity of cybersecurity solutions and their costs, utilities need to leverage resources readily available to them. AWWA has developed cybersecurity tools and guidance for this purpose that can be viewed on the association’s Cybersecurity & Guidance webpage. Water ISAC provides current information on the latest threat tactics. Information can also be found through the US Environmental Protection Agency and the Cybersecurity and Infrastructure Security Agency.
Despite the guidance and tools available to utilities, assessing and mitigating cyberthreats requires trained personnel capable of understanding and acting on the information. A reputable, experienced cybersecurity consultant can also help navigate and cost-effectively mitigate cyberthreats.
Originally published in the Journal for American Water Works Association, April 2022.